How Does RFID Transmit Key to Module? (Spoiler: It Doesn’t.)
That question—how does RFID transmit key to module—comes up a lot when clients first design a secure access system. The wording itself hints at a common misunderstanding. In a properly engineered system, the secret cryptographic key is never, ever transmitted from the tag to the reader module. If it were, the system would be fundamentally broken. Let’s walk through what actually happens.
Think of it like a speakeasy password in the 1920s. The bouncer (reader) doesn’t have a list of passwords. Instead, he gives you a random challenge phrase, like “The weather in Chicago.” You (the tag) know a secret rule—say, to respond with the third word of the challenge plus your secret code name. If you reply correctly, you’re in. Your secret code name (the key) was never spoken aloud.
In RFID terms, this is a challenge-response protocol in access control. Here’s the technical sequence you’d see when integrating:
- RFID Reader Sends a Random Number: The reader’s secure crypto RFID module generates a completely random, one-time-use number (the challenge) and beams it to the RFID tags.
- Tag Does Math Internally: The tag’s secure silicon chip receives this number. Inside its locked hardware vault, it fetches its immutable secret key. It then crunches both numbers through a certified encryption algorithm (like AES-128). The key never leaves this vault.
- Tag Returns the Result, Not the Key: The tag transmits only the encrypted result of that calculation back to the reader.
- Reader Verifies Independently: The reader’s module does the same math locally, using the same random number and the secret key it has on file for that specific tag ID. If the result it computes matches the result the tag sent back, authentication is successful. This entire secure RFID authentication handshake process proves the tag knows the key without exposing it.
Why This Distinction is Critical for Your Project
If you’re sourcing parts for a warehouse inventory scan, this is overkill. But if you’re securing a pharmaceutical lab or a corporate data center, it’s everything. Here’s the practical takeaway:
- The “Module” is a Secure Vault: The “module” isn’t just a circuit; it’s a certified secure element (often called an SE or HSM-lite). This is why RFID keys stay in hardware. The reader’s main CPU shouldn’t even have direct access to the raw keys.
- Look for Specific Certifications: When buying tags, don’t just look for “encrypted.” Look for specifics like “MIFARE DESFire EV3” or “AES-128 secure authentication.” These implement the handshake described above.
- Avoid Systems That “Transmit Keys”: If a vendor’s datasheet implies keys are sent wirelessly, steer clear. That’s a legacy or low-security method vulnerable to replay attacks.
So, the accurate answer to how does RFID transmit key to module is simple: it doesn’t. The system is designed so the key’s presence is proven through cryptography, not revealed through transmission. Implementing high-security RFID with crypto tags means investing in this hardware-based handshake, which is the only way to reliably move beyond simple ID cloning to true authentication.
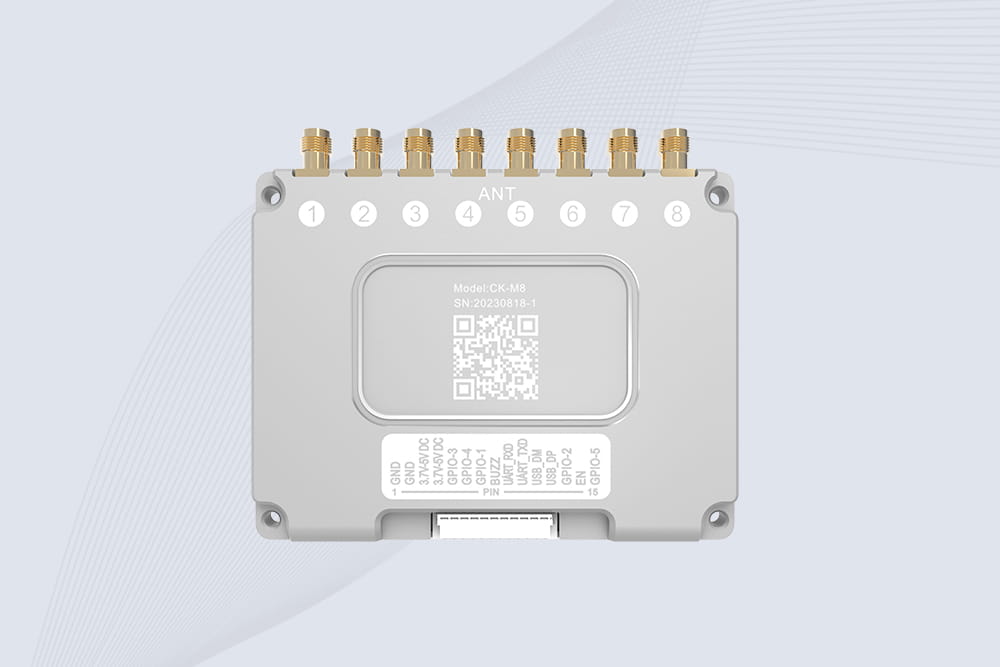
RFID Module Recommendation
 Cykeo RFID IoT Solution Products R&D Manufacturer
Cykeo RFID IoT Solution Products R&D Manufacturer