How to Choose Between Active and Passive Long-Range RFID Readers?
592Understand the differences between active and passive long-range RFID readers. Learn how to select the best option for your needs with Cykeo’s expert guidance.
MoreAll RFID Product
Transferring RFID tag data to a MySQL database involves capturing tag IDs via an RFID reader, structuring your database, and integrating middleware or scripts to automate data flow. This process is critical for asset tracking, inventory management, and real-time analytics. Here’s a detailed guide to streamline this workflow.
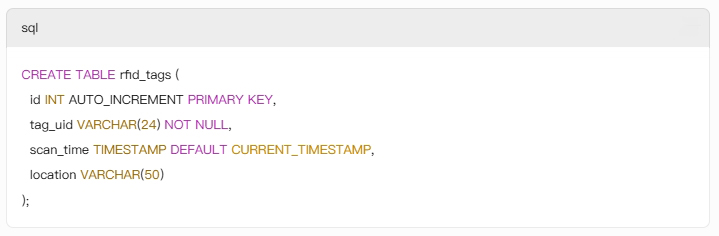
tag_uid and scan_time for faster queries.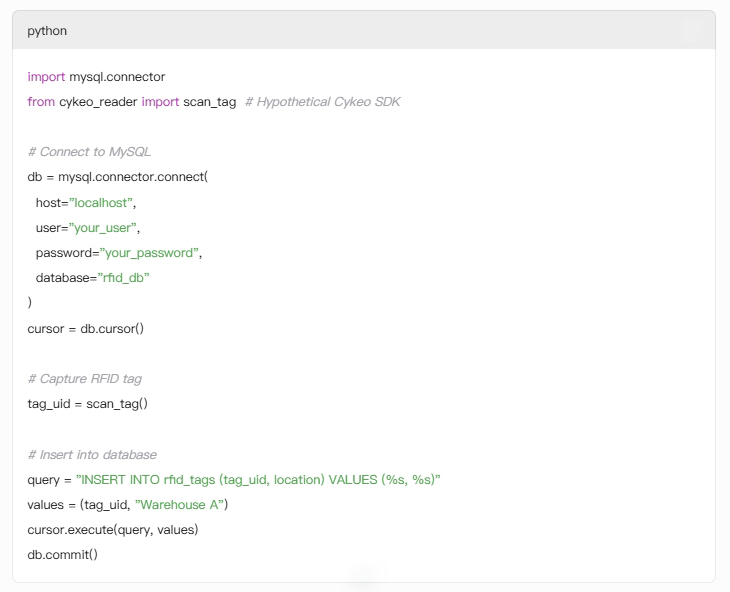
try-except blocks to log failed inserts and retry transmissions.EXPLAIN in MySQL to optimize slow queries.A manufacturing plant automated tool tracking using Cykeo’s RFID-to-MySQL pipeline, reducing audit times from 5 hours to 30 minutes with 99.9% accuracy.
Understand the differences between active and passive long-range RFID readers. Learn how to select the best option for your needs with Cykeo’s expert guidance.
MoreWondering how do RFID tags modulate data? We explain the practical backscatter method used by passive tags and how it impacts your real-world system performance.
MorePuchase RFID antennas? The article discuss key design for RFID system integrators, solution providers,help you Choose suitable rfid antennas .
MoreLearn what type of antenna passive RFID tags use. We clarify the difference between coil antennas for proximity and printed dipoles for UHF logistics tracking.
More