How We Actually Track Laptops in Enterprises with RFID—Lessons from LA Labs to Brooklyn R&D Centers
303Candid insights into using RFID for enterprise laptop tracking—real projects, mistakes, shortcuts, and lessons from LA and Brooklyn.
MoreAll RFID Product
As the demand for digital and intelligent management continues to grow, the RFID Check-In Check-Out System is becoming the preferred choice across industries for managing the movement of people and goods. With its efficiency, accuracy, and convenience, this system helps foreign trade clients understand the technical value and seize market opportunities. It enables governments, institutions, and enterprises to deliver high-quality smart management solutions. The following sections provide a detailed analysis of the system’s working principles, application scenarios, and advantages.

The RFID Check-In Check-Out System uses radio frequency identification technology to automatically record and manage the movement of people and assets through RFID tag recognition. The system consists of RFID tags, readers, antennas, and backend management software. Its key advantages include:
High Efficiency: The system identifies tags without physical contact. People don’t need to stop to check in or out, significantly increasing throughput, especially in high-traffic areas.
High Accuracy: It achieves over 99% accuracy, eliminating errors and omissions that are common in manual records.
Real-Time Monitoring: The backend displays the real-time entry and exit status and location of personnel and goods, enabling managers to track activities effectively.
Strong Scalability: You can integrate the system with access control, attendance, and security systems to achieve unified management.
The RFID Check-In Check-Out System operates through the interaction of radio signals. When a person or item carrying an RFID tag enters the signal range of a reader, the reader emits a specific frequency signal through the antenna to activate the tag. Once activated, the tag modulates and returns its stored unique identification information. The reader decodes the signal and transmits the tag data to the backend software. The software checks the information against preset permissions to determine whether the person or item is authorized to enter or exit. If approved, the system records the time, location, and other data and may open doors or trigger notifications. If access is denied, the system triggers an alert.

Corporate Offices: Employees check in and out with RFID tags. The system integrates with attendance systems to automatically calculate work hours, supporting payroll. It can also manage visitor access for security.
Schools and Training Institutions: Students use RFID tags to check in and out of school or classrooms. Parents receive real-time notifications about student arrivals and departures. During exams, the system verifies student identity to prevent cheating.
Hotels and Resorts: Guests receive RFID room cards for contactless door access and in-hotel purchases. Employees use RFID tags for controlled access to work areas.
Warehousing and Logistics: Goods entering or leaving warehouses are automatically registered using RFID tags, updating inventory in real time and improving logistics management.
Exhibitions and Events: Attendees use RFID badges to check in quickly. Organizers monitor crowd flow and optimize event management.

Early Planning: Define requirements, determine installation locations and signal coverage, and design a logical system architecture.
Hardware Deployment: Choose appropriate RFID readers and tags based on the environment. Ensure full coverage without dead zones and install wiring to maintain system stability.
Data Entry and Permission Settings: Enter personnel and item data into the backend system and assign permission levels to maintain secure management.
System Testing and Training: Fully test all functions before launching. Train both administrators and users to ensure proper system usage.
Performance Assessment: Evaluate reading distance, speed, and multi-tag reading capabilities to match the actual use case.
Compatibility: Choose systems that integrate well with existing platforms like ERP or OA systems to avoid data silos.
Security Features: Ensure the system includes encryption, permission control, and environmental protection features such as waterproofing and dustproofing.
After-Sales Support: Select suppliers that offer installation, configuration, training, and 24/7 technical support to reduce operational risk.
RFID Check-In Check-Out Systems bring efficiency and automation to multiple industries. Whether you’re improving enterprise management or enhancing service delivery in institutions, this system offers significant value. If you have procurement needs or technical questions regarding the RFID Check-In Check-Out System, feel free to contact us anytime.

CYKEO Embedded RFID Modules are designed for compact industrial and IoT devices that require stable UHF performance. These UHF RFID Modules support global protocols, flexible power control, and reliable multi-tag reading for smart cabinets, production lines, and asset tracking systems.
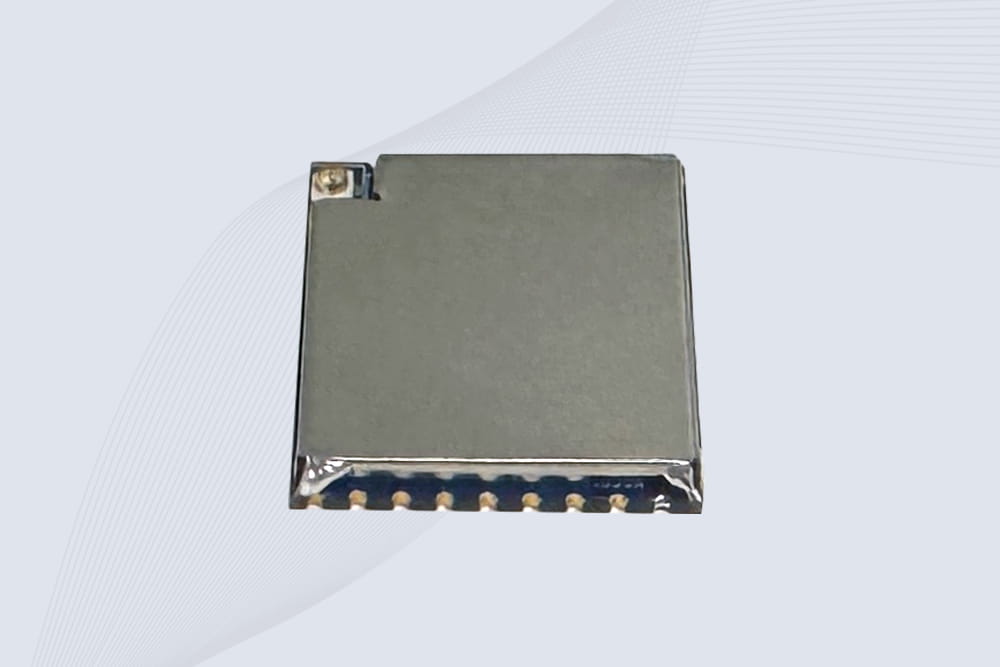
CYKEO Embedded RFID Module is built for compact IoT and industrial devices that need stable UHF performance. This UHF module supports global protocols, low power operation, and reliable multi-tag reading for smart lockers, production lines, and always-on RFID systems.

CYKEO CYKEO-M1 drone rfid module is a compact UHF RFID reader module designed for drones and UAV platforms. It supports long-range aerial scanning, fast multi-tag reading, and stable performance in wind, vibration, and outdoor environments.

CYKEO CYKEO-M4 RC522 RFID Module is an industrial-grade UHF RFID reader with 4 ports, supporting ISO, EPC, and GB protocols. High-speed, accurate reading for IoT, automation, and warehouse applications.
Candid insights into using RFID for enterprise laptop tracking—real projects, mistakes, shortcuts, and lessons from LA and Brooklyn.
MoreCompare QR codes and NFC/RFID tags for your business. Discover their pros and cons in cost, security, and usability to choose the right identification technology.
MoreDiscover the real-world advantages of UHF integrated readers — compact design, fewer cables, and stable performance. Learn how RFID engineers use them with Cykeo RFID handheld readers and tags for smooth, reliable industrial automation.
MoreDiscover how RFID tags enhance automotive security, streamline maintenance, and improve user experiences. Explore Cykeo’s RFID solutions for modern vehicles.
More