Where is the RFID Reader on an iPhone?
61Wondering where is the RFID reader on an iPhone? Understand iPhone's NFC capabilities, its location, limitations, and see professional RFID solutions from CYKEO.
MoreAll RFID Product
When you hear the term rfid wireless theft, it might sound like something from a cyber-crime movie. A thief just walks by with a hidden reader, and suddenly your hotel key card or retail tag is cloned. Unfortunately, that’s not entirely fiction. From hotel doors being opened with cloned MIFARE Classic cards to organized shoplifting rings exploiting poorly secured RFID systems, the threat is real.
RFID is everywhere—your office badge, the chip inside your gym membership, even that little tag on a pair of jeans at the mall. The beauty of RFID is also its weakness: it works wirelessly. That means a legitimate reader can scan a card at a distance… but so can a malicious one. Skimming devices small enough to hide in a backpack have already been reported, which is why some states, like California, made RFID skimming a crime.

And it’s not only the “guys with hidden readers.” Researchers found actual hardware backdoors in some widely used RFID chips, meaning you didn’t even need to guess the encryption—cards could be cloned in minutes. Imagine a hotel chain using those cards worldwide. That’s a hacker’s jackpot.
While we often think about RFID theft as hackers stealing card data, in retail the story flips. Big brands like Macy’s use RFID chips to track products and fight theft. The logic is simple: if a jacket leaves the store without passing through checkout, the system knows. Some even pair RFID with computer vision, or build “smart shelves” that notice when items vanish in bulk.
But here’s the catch—what helps stop shoplifters can sometimes raise privacy questions. If RFID tags stay active after purchase, technically they can be scanned outside the store too. Convenience versus surveillance, it’s always a trade-off.
To fight back against RFID wireless theft, researchers and engineers keep coming up with tricks. Some solutions encrypt the communication between tag and reader, adding rolling keys or random numbers so cloning isn’t easy. Others, like in the DVD industry, use RFID to “lock” the product—stolen items won’t even work until they’re activated at checkout. It’s clever, turning the technology against the thieves.

Meanwhile, startups push out real-time alerts: a tag leaves a storage area and your phone buzzes instantly. Or in warehouses, RFID plus motion sensors can spot tampering before items actually disappear.
So is RFID wireless theft a deal-breaker? Not really. The technology is too useful to abandon—supply chains, ticketing systems, even contactless payments rely on it. But it does force us to be smarter. Don’t assume your RFID card is unbreakable. Don’t assume every tag is harmless after you buy the product. And if you’re deploying RFID in your business, think of it like leaving doors unlocked—yes, it works fine until someone tries the handle.
At the end of the day, RFID isn’t the problem. It’s the way we secure it—or fail to. And knowing that is the first step to keeping both doors and data safe.
Cykeo’s CYKEO-T1D industrial RFID ceiling reader features 500 tags/sec scanning, IP54 protection, and -20℃~60℃ operation for retail/warehouse security. Supports ISO18000-6C and GB/T29768 protocols.

Cykeo’s ceiling-mounted RFID reader enables hands-free 5m inventory tracking with 500 tags/min speed. Features dual alerts, ERP integration, and IP54 rating for warehouse security.
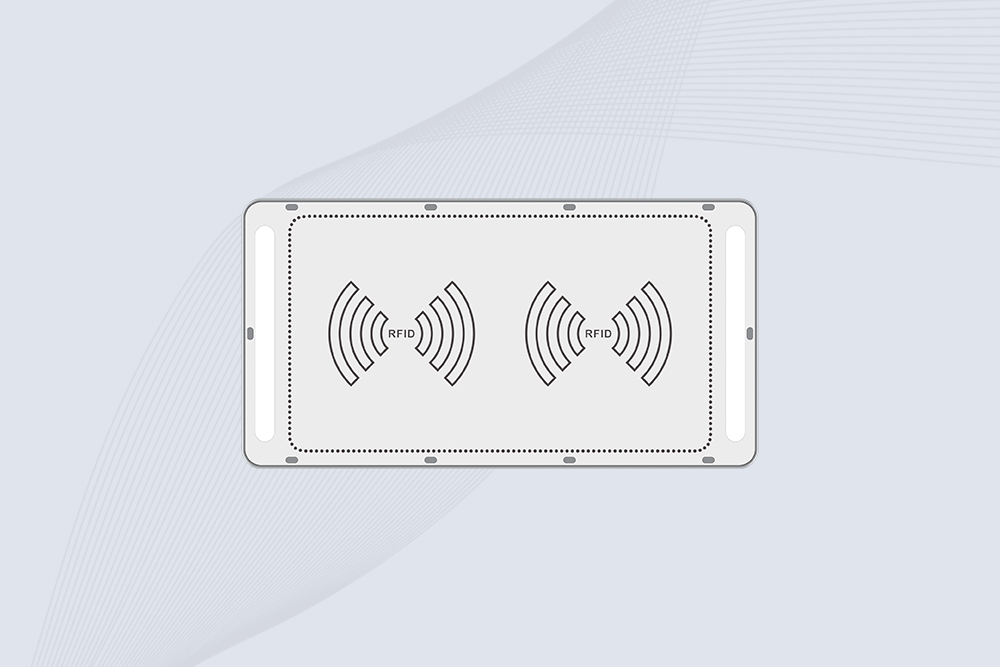
Cykeo CK-T1E RFID gate system features 120° coverage, AI motion filtering, and 5m detection for retail/warehouse security. IP67 rugged design with ERP integration.
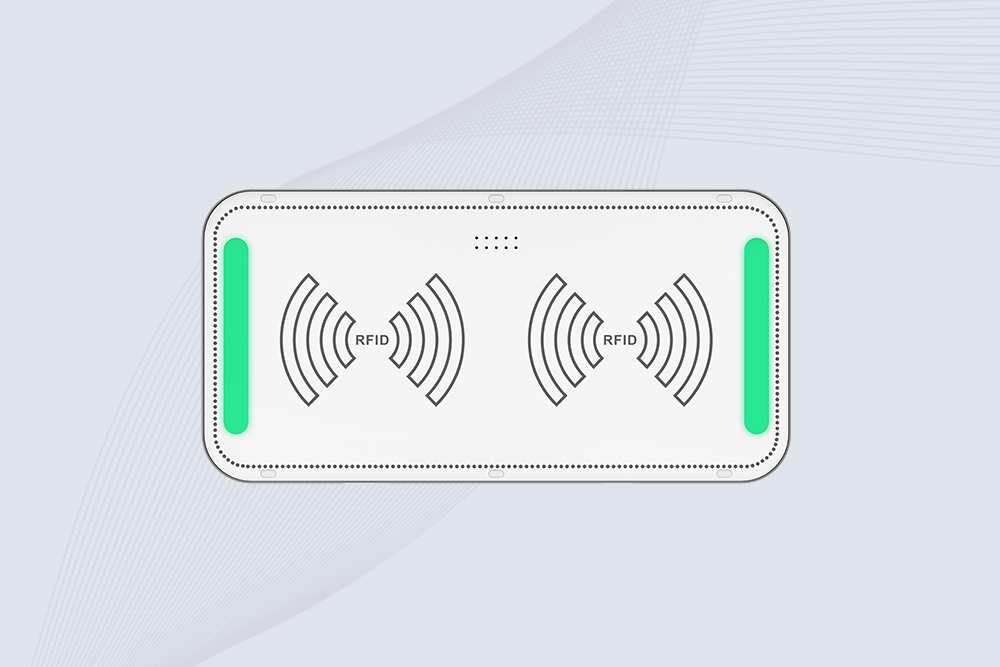
Cykeo CYKEO-T1A industrial ceiling RFID system offers 10-20m read range, 500+ tags/sec speed, and IP65 protection for smart warehousing. Supports multi-protocol integration and real-time inventory alerts.
Wondering where is the RFID reader on an iPhone? Understand iPhone's NFC capabilities, its location, limitations, and see professional RFID solutions from CYKEO.
MoreLearn how to deploy multi-reader RFID systems for seamless warehouse coverage. Optimize placement, avoid interference, and integrate Cykeo’s solutions for maximum efficiency.
MoreStruggling to set up a USB RFID reader on Windows 10 or 11? Follow this step-by-step guide to install drivers, troubleshoot errors, and start scanning tags fast.
MoreHigh temperature RFID tags explained from real industrial use: heat limits, materials, failures, costs, and where heat-resistant RFID truly works.
More