Who Are the Main Companies Manufacturing and Distributing RFID Chips?
983Discover the leading companies manufacturing and distributing RFID chips globally. Explore their specialties and how Cykeo delivers innovative RFID solutions.
MoreAll RFID Product
Talking about como programar RFID access control sounds simple, but once you face the reader, the cards, and the controller, all kinds of questions pop up. It’s not the same to build a DIY prototype with Arduino as it is to deploy a commercial system with hundreds of credentials. Here I’ll walk you through the process in a clear way, with real-world examples, so you don’t waste time or cards.
Before jumping into programming, you need to know the building blocks. RFID access systems can run on different frequencies:
Also, a card is not just a number. It has a unique UID and, in some cases, memory banks (EPC, User, etc.). Deciding where to write data is part of the process.
If your goal is to learn or build something small, the quickest route is using an RC522 RFID module with Arduino. With just a few lines of code you can read a card’s UID, compare it to an approved list, and trigger a relay that opens a lock. The workflow looks like this:
It’s not the most elegant setup, but it works and gives you a solid foundation.
Most standalone controllers have a similar approach: you enter programming mode with a master code, present a card to enroll it, and you’re done. Removing users works with a similar sequence.
In more advanced systems, enrollment is managed through software. You plug in a USB programmer, select the card in the application, write its ID, and sync with the access control database.
A typical mistake is trying to write on a card that doesn’t support it. Another is mixing frequencies (for example, using a 125 kHz reader with a 13.56 MHz card). People also tend to rely only on the UID, when for critical systems you should use encrypted credentials.
Programming an RFID access system isn’t magic, but it’s not just “tap a card” either. Knowing como programar RFID access control means understanding your hardware, the credential enrollment process, and the security measures you need. Whether you’re building a small Arduino prototype or configuring a building-wide system with management software, the key is to handle the writing process carefully, validate each step, and follow good practices.
That way, you’ll end up with a system that doesn’t just open doors, but does it reliably and securely.
Cykeo’s CYKEO-T1D industrial RFID ceiling reader features 500 tags/sec scanning, IP54 protection, and -20℃~60℃ operation for retail/warehouse security. Supports ISO18000-6C and GB/T29768 protocols.

Cykeo’s ceiling-mounted RFID reader enables hands-free 5m inventory tracking with 500 tags/min speed. Features dual alerts, ERP integration, and IP54 rating for warehouse security.
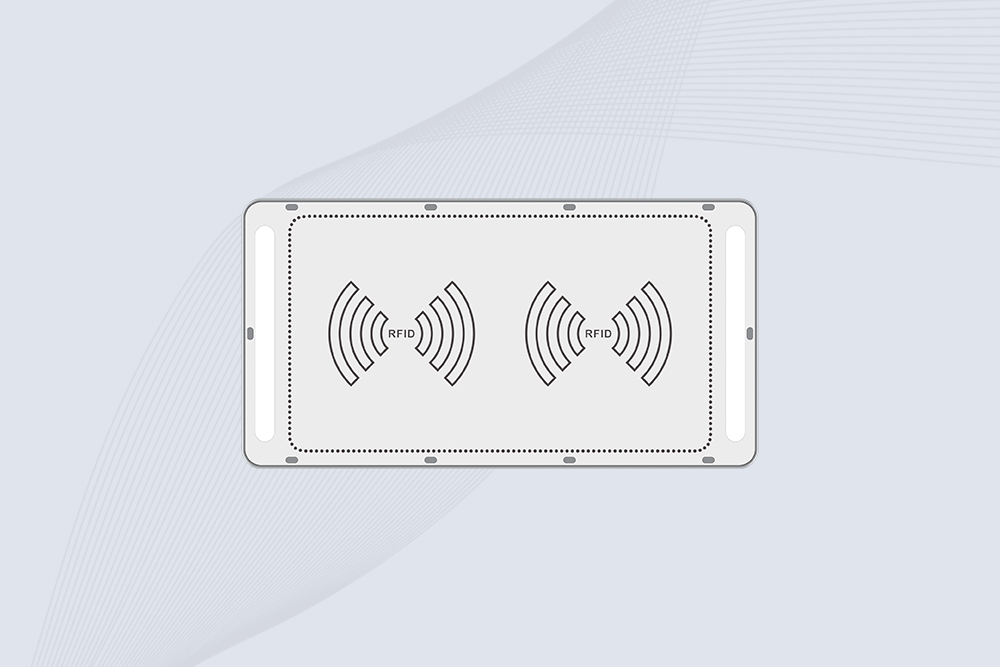
Cykeo CK-T1E RFID gate system features 120° coverage, AI motion filtering, and 5m detection for retail/warehouse security. IP67 rugged design with ERP integration.
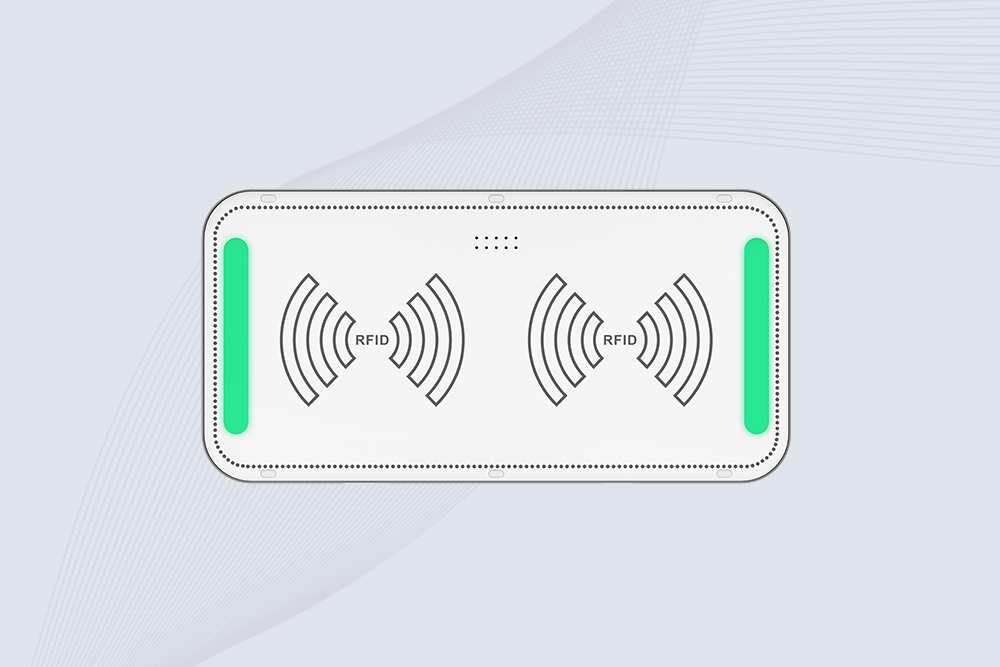
Cykeo CYKEO-T1A industrial ceiling RFID system offers 10-20m read range, 500+ tags/sec speed, and IP65 protection for smart warehousing. Supports multi-protocol integration and real-time inventory alerts.
Discover the leading companies manufacturing and distributing RFID chips globally. Explore their specialties and how Cykeo delivers innovative RFID solutions.
MoreDiscover whether GPS or RFID is the most effective technology for tracking inventory in stores. Compare accuracy, cost, and use cases for retail operations.
MoreLearn how to use RFID module with Arduino step-by-step. This beginner-friendly CYKEO tutorial covers wiring, coding, and project ideas for RFID-RC522.
MoreRFID tagging systems, leveraging advanced radio frequency identification technology, offer an accurate, efficient, and intelligent management solution,
More